I have developed a fast emulator for modern shellcodes, that perform huge loops of millions of instructions emulated for resolving API or for other stuff.
The emulator is in Rust and all the few dependencies as well, so the rust safety is good for emulating malware.
There are shellcodes that can be emulated from the beginning to the end, but when this is not possible the tool has many features that can be used like a console, a memory tracing, register tracing, and so on.
https://github.com/sha0coder/scemu
In less than two seconds we have emulated 7 millions of instructions arriving to the recv.
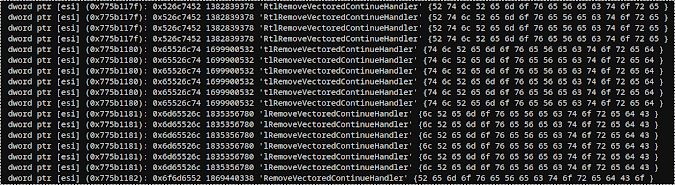
At this point we have some IOC like the ip:port where it's connecting and other details.
Lets see what happens after the recv() spawning a console at position: 7,012,204
target/release/scemu -f shellcodes/shikata.bin -vv -c 7012204
The "ret" instruction is going to jump to the buffer read with recv() so is a kind of stager.
The option "-e" or "--endpoint" is not ready for now, but it will allow to proxy the calls to get the next stage automatically, but for now we have the details to get the stage.
SCEMU also identify all the Linux syscalls for 32bits shellcodes:
The encoder used in shellgen is also supported https://github.com/MarioVilas/shellgen
Let's check with cobalt-strike:
In verbose mode we could do several greps to see the calls and correlate with ghidra/ida/radare or for example grep the branches to study the emulation flow.
target/release/scemu -f shellcodes/rshell_sgn.bin -vv | grep j
target/release/scemu -f shellcodes/rshell_sgn.bin -vv -c 44000 -l
- Hacker Tools
- Computer Hacker
- Hacker Tools Mac
- Pentest Tools Android
- Nsa Hack Tools
- Pentest Recon Tools
- Nsa Hacker Tools
- Nsa Hacker Tools
- What Is Hacking Tools
- Pentest Tools Subdomain
- Hack Tools Download
- Pentest Tools For Mac
- Pentest Tools For Windows
- Hack Tool Apk No Root
- Hack Tools For Pc
- Hack Tool Apk No Root
- Hacking Tools Mac
- Physical Pentest Tools
- Hacker
- Hacker Tools Apk Download
- Hack Tools Mac
- Bluetooth Hacking Tools Kali
- Pentest Tools For Mac
- Hacker Tools Mac
- Underground Hacker Sites
- Pentest Tools Bluekeep
- Hacking Tools For Windows
- Hacker Hardware Tools
- Pentest Tools For Android
- Hacking Tools Online
- Hack Tools
- Hackers Toolbox
- Pentest Tools Port Scanner
- Underground Hacker Sites
- Tools 4 Hack
- Termux Hacking Tools 2019
- Hacking Tools Github
- Pentest Tools Alternative
- Pentest Reporting Tools
- Best Hacking Tools 2019
- Hacking Tools Usb
- Pentest Tools Apk
- How To Hack
- Pentest Tools Website Vulnerability
- Pentest Tools Url Fuzzer
- Hacking Apps
- Hack Tools For Pc
- Nsa Hacker Tools
- Hacking Tools
- Hacking Tools For Windows
- Android Hack Tools Github
- Underground Hacker Sites
- Pentest Tools Linux
- Pentest Tools Android
- Hacker Tools Free
- Ethical Hacker Tools
- Pentest Tools For Android
- Hacking Tools Free Download
- Termux Hacking Tools 2019
- Top Pentest Tools
- Top Pentest Tools
- Hacking Tools And Software
- Github Hacking Tools
- Pentest Tools Bluekeep
- Hack Tools Pc
- Pentest Tools Find Subdomains
- World No 1 Hacker Software
- Hacking Tools
- Pentest Tools Free
- Termux Hacking Tools 2019
- Hacker Tools Online
- Top Pentest Tools
- Pentest Tools Alternative
- Hacking Tools Windows
- Pentest Tools Bluekeep
- Pentest Tools Open Source
- Game Hacking
- Pentest Tools Apk
- Hacking Tools Usb
- Nsa Hack Tools
- Game Hacking
- What Are Hacking Tools
- Nsa Hacker Tools
- Hacking Tools For Pc
- Hacker Tools Free
- Hacking Tools For Games
- Easy Hack Tools
- Hacker Tools Windows
- Pentest Tools Subdomain
- Usb Pentest Tools
- Pentest Tools Subdomain
- Hacking Tools Download
- Hacking Tools Windows
- Github Hacking Tools
- How To Hack
- Pentest Tools Github
- Beginner Hacker Tools
- Pentest Tools Tcp Port Scanner
- Hacker Tools For Mac
- World No 1 Hacker Software
- Hack Tools For Games
- Hack Rom Tools
- Game Hacking
- Hacker Tools Hardware
- How To Install Pentest Tools In Ubuntu
- Hacking Tools Online
- Hacking Tools For Kali Linux
- Hacker Tools Online
- Hacking Tools
- Hacker Tools Mac
- Pentest Box Tools Download
- Hackrf Tools
- Bluetooth Hacking Tools Kali
- Hack Tool Apk No Root
- Hacking Tools Download
- New Hack Tools
- Hacking Apps
- Pentest Tools Android
- Hack Tools Github
- What Are Hacking Tools
- Hack Tools Online
- Hacking Tools 2019
- Hacking Apps
- Pentest Box Tools Download
- Hacking Tools Pc
- Pentest Tools Nmap
- Pentest Tools Url Fuzzer
- How To Make Hacking Tools
- Hacker Tools Github
- Pentest Tools Review
- Hack Tools Github
- Pentest Tools Website
- Nsa Hacker Tools
- Pentest Tools For Windows
- Hack Tools For Windows
- Pentest Tools











No comments:
Post a Comment